Constant threat protection with SOC as a Service
Fully managed expert-level incident handling for quick response and 24/7/365 protection of your digital assets.
Why does your business need SOC as a Service?
Enhance security posture and experience superior security outcomes without burdening your IT team. Cut through the noise, prioritise what matters and stop attacks as soon as they begin.

Reduce
Risks and Cost
Minimise capital and labour expenditure by allowing our highly trained cyber experts to monitor systems for you. Neutralise threats and investigate incidents with flexible payment plans that fit your business and budget.

Access Advanced Threat Intelligence
Lumen Black Lotus Labs® uses expert research, machine learning and automation to analyse billions of internet activity data points daily. Leverage our unmatched threat intelligence to identify and block suspicious attack patterns before they reach your organisation.

Improve
Post-Incident Analysis
Receive detailed reports about trends, threats and lessons learned for a deeper investigation of incident cause and impact. Receive log analysis reports, validate priority and apply remediation recommendations for long-lasting benefit and improvement.

Customise Service to your Requirements
Leverage existing security investments made by your organisation. Our team will work with you to develop and maintain a runbook and customised SOC based on your specific use case requirements and security priorities.
Managed security operations centre for hassle-free threat detection and response
Avoid the expense and effort needed to build and maintain an in-house Security Operation Centre. Instead, augment your security strategy with world-class expertise and cutting-edge technology that detects and analyses cybersecurity threats for you.
Learn more about Lumen SOC as a Service
What is Lumen SOC as a Service?
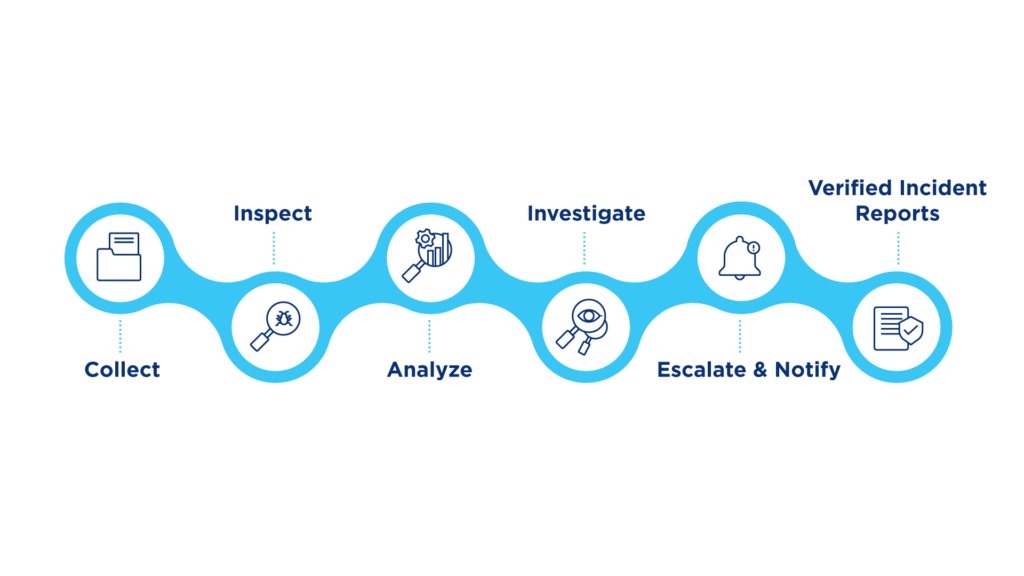
Lumen SOC as a Service provides 24/7/365 incident handling, threat detection, and response. The service features include:
- Security information and event management (SIEM) on supported SIEM standard platforms like IBM QRadar, Splunk, Sentinel, LogRhythm and FortiSiem.
- Development and tuning of use cases that adhere to the MITRE ATT&CK framework.
- Run book development and maintenance of procedures for handling alerts and incidents.
- Deep-dive analytics of trends, impact and lessons from every incident.
- Advanced threat hunting to discover anomalies related to current global security events
- 10 global SOCs, out of which, 3 are located in Asia Pacific: Singapore, Australia and India.
How does Lumen SOC as a Service work?
Lumen SOC as a Service is offered in three package options, with flexible pricing based on the maximum amount of monthly incidents as determined by you. A kickoff meeting occurs after the contract signature to scope out deliverables and timing. Initially, we gather information, access your existing security and operational environment, identify critical use cases and develop the run book.
Once set up, our security team logs in daily to your SIEM platform and monitors it continuously for security events. Lumen also offers proactive threat hunting, where the expert reviews your system based on current trends to discover anomalies outside established use cases. Our APAC SOCs handle over 100,000 alerts per month and monitor 5,000+ devices, fully managed by our operational teams that include:
- SOC Analysts – Security Monitoring
- Threat Analysts – Threat Hunting and Operations Research (THOR) and Digital Risk Protection Services (DRPS)
- Platform Engineering – Support and maintenance of SIEM and Security Orchestration, Automation and Response (SOAR) platforms
- Automation Engineering – Support SOAR automations
- Security Advisory Consulting
What happens in case of an incident?
If an incident is identified, our SOC analyst will classify, triage, and analyse the event. We first analyse logs to isolate incidents and validate if the event is true or a false positive. We only prioritise and send true event alerts to you. Our event alerts come with deep-dive analytics related to threats, trends and lessons from the past. We also provide remediation recommendations so you can enhance your response.
SOC as a Service FAQs
What is SOC as a Service?
A Security Operations Centre (SOC) is a team of security experts that use specialised software to monitor and analyse an organisation’s security posture, detect and respond to threats and prevent security breaches. The SOC software takes in telemetry data from across an organisation’s IT infrastructure and generates alerts for the experts to act upon. For example, the software detects malware at a network endpoint, and the security team shuts down and deletes the malware before it infects more devices.
SOC as a Service or SOCaaS is the process of outsourcing SOC functions to a third-party provider. The service provider runs and manages a virtual SOC using cloud-based services, so you don’t have to do it internally.
Why choose SOC as a Service instead of building one internally?
Building and maintaining an in-house SOC is an expensive and time-consuming process. You must hire and retain experienced professionals who can choose the right technology and manage your SOC to the standards expected by your customers and industry regulators. It requires a certain level of security maturity and capabilities before you can get started.
Even organisations that put in the effort can struggle to keep up with the ever-changing threat landscape. Justifying a large security training and technology budget is hard when security is not your main business function.
In contrast, a SOCaaS provider always has access to cutting-edge technology, experience and expertise because they meet SLAs and protect assets for a wide range of organisations and industries. You get enhanced threat protection and deep analytics while minimising cost and effort.
What types of threats does a SOC as a Service protect you from?
A SOC as a Service protects you from all types of network threats like ransomware, malware, distributed denial of service(DDoS), credential theft, data leaks, zero-day threats and more. The service provider continuously monitors your entire IT infrastructure for suspicious internal and external activity. You receive early alerts for activities like:
- Repeated application requests coming from a single IP address.
- Requests coming from globally marked scam IPs.
- Unusual or repeat login attempts.
The SOCaaS provider will filter and present alerts in context so you can action them with confidence.
Lumen Library
Insights and Resources
Questions? Let’s talk.
Contact our team and get answers you’re looking for.






