Enterprise Grade Cloud Security Managed for You
Experience enhanced visibility, threat intelligence and control with our zero-trust approach to public cloud security.
Why does your business need Cloud Security Management?
Cloud security becomes complex due to distributed, changing environments and unlimited endpoints with complex configurations. Lumen Managed Cloud Security combines advanced technology with human expertise to provide comprehensive protection and prevent oversights.

Agile and Secure Modernisation
Accelerate business growth with cloud architecture that optimises security and efficiency. Our dedicated cloud experts help you implement and migrate your critical workloads to the cloud without compromising security.

Improved Visibility and Control
Deploy single or multiple public cloud environments via a single, centrally managed platform. Enhance visibility, configuration control and overall governance standards in every cloud.

24/7 Threat Protection
Automated threat-hunting algorithms review network and user activities to detect and remediate cyber threats in real-time. Round-the-clock vulnerability scanning, threat detection, incident response and event management secure all your cloud workloads.

Remove Operational Complexity
Deploy applications and implement policies on-premises or in the public cloud. Unify network and security management from edge to public cloud for on-site and remote users.
Award-winning cloud security managed services for every business
Embrace the move to the cloud with centralised security and flexible access controls. Build cloud-first architecture centred around zero-trust security principles.
Learn more about Lumen Cloud Security Managed Services
What is Lumen Cloud Security Managed Service?
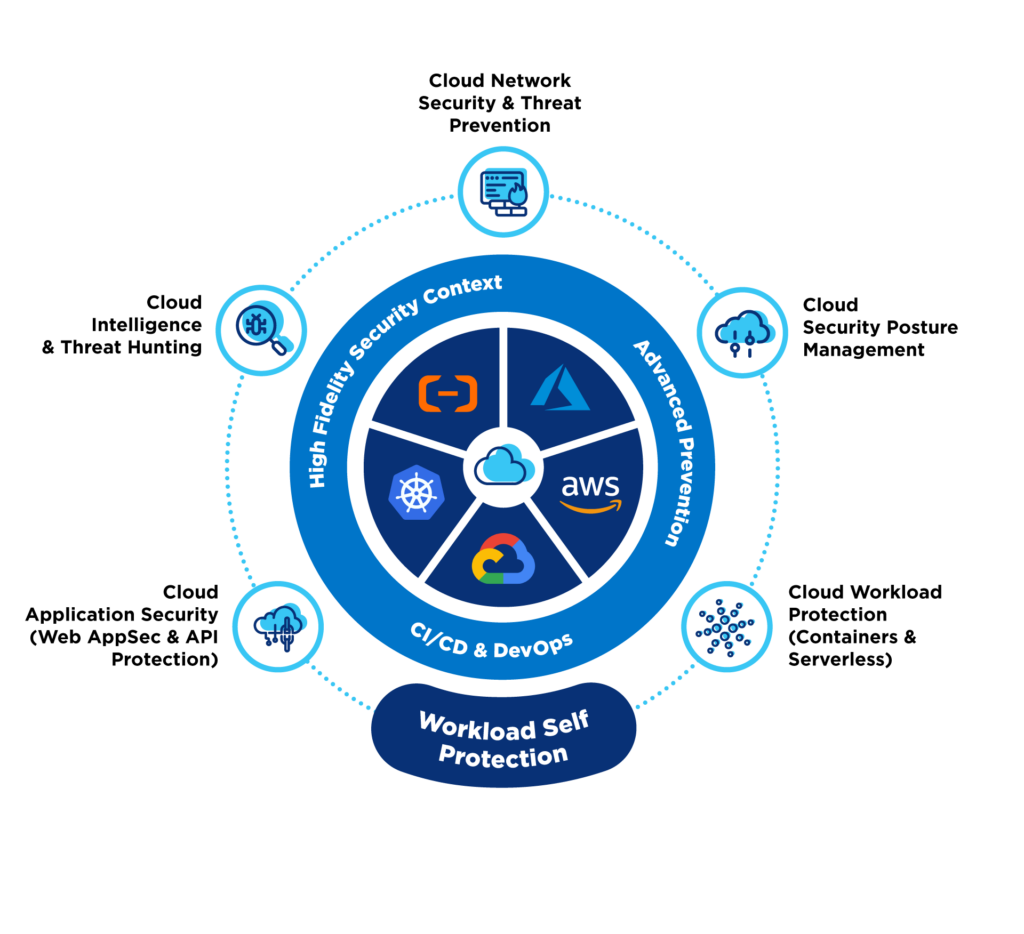
Lumen Cloud Security Managed Services combine in-house expertise with third-party vendor partner software to meet your cloud security needs. They include:
- Non-intrusive and agentless scanning with complete coverage of all services on your cloud estate – including Amazon Web Services, Microsoft Azure, Alibaba Cloud and Oracle Cloud.
- Misconfiguration detection by inspecting against configuration controls, including CIS control benchmarks & other frameworks.
- Malware scans using both signature-based and heuristic approaches out of band.
- Asset inventory and sensitive data detection across workload and control plane.
- Identity and access management, including identity misconfigurations, ensuring least-privilege compliance and monitoring identity hygiene metrics.
Our in-house security experts analyse your existing cloud security posture and suggest enhancements to close gaps and improve compliance.
How does Lumen cloud security management work?
At Lumen, we augment your security operations to enhance risk management and protection. We configure, operate, and run agentless, non-intrusive scans through a cloud security platform. You will receive weekly reports on cloud security posture using customised queries and the dashboard feature.
Lumen’s Security Consultants analyse the outcome of the scans, contextualise and prioritise risks, and advise on remediation, isolation and control. We also provide a virtual security operations centre (SOC) to escalate on exception for high severity risks identified during scanning. You gain deep security visibility on vulnerabilities, attack paths, non-secure configurations and compromised assets.
Cloud Security Managed Services FAQs
What are cloud security managed services?
Cloud security is an umbrella term for the tools, technologies, procedures and policies essential for protecting your applications, their users and sensitive data residing in the cloud. Cloud security managed services refer to outsourcing security capabilities to an external third party. The provider handles all your cloud protection requirements, so you can focus on what you do best — enhancing your customer experience!
Why are cloud security managed services important?
It is challenging to build cloud security capabilities in-house due to the complexity of the cloud’s attack surface. Public-facing applications are also vulnerable to network threats, irrespective of where they are hosted. Despite heavy expenditure and in-house resources, many organisations experience deadly cyberattacks due to incorrect configurations, unsecured API endpoints or poorly managed access control. Improperly handled cloud security can negatively impact application performance while failing to provide sufficient protection.
Managed cloud security is a stress-free and efficient approach to cloud security. Third-party security experts handle all your security requirements in a customised and cost-effective way. You have total control and flexibility over how your security requirements are met for your specific cloud environment.
Why do you need cloud security management in the public cloud?
Public cloud security follows the shared responsibility model. The public cloud provider is responsible for the security of the cloud, but as the cloud user, you are responsible for security in the cloud. You have complete responsibility over your data, access control and configuration of public cloud services.
It’s common to inadvertently increase security risks when setting up and using your public cloud environment. For example, developers who spin up resources without approval can expose endpoints to cybercriminals. Managed cloud security helps you identify gaps and establish governance policies that regulate how your public cloud environment is configured, accessed and managed. It ensures your team can access what they need to get work done without inadvertently causing security failures.
What are the challenges in self-managing public cloud security risks?
Cloud technology is continuously evolving and every new services has different configuration and access control requirements. Staying up-to-date with the latest cloud security requirements is challenging.
Comprehensive public cloud security also requires too many tools and competencies. For example:
- API security tool to discover inventory of existing API connections, API exposures, and unknown APIs.
- Cloud Identity & Entitlement Management (CIEM) to detect identity misconfigurations.
- Cloud Workload Protection Platforms (CWPP) to protect cloud servers/VMs, containers, serverless functions across clouds.
- Cloud Security Posture Management (CSPM) to monitor cloud apps, services, containers, to detect misconfigurations or incorrectly enforced policies.
- Container and Kubernetes Security.
- Cloud Detection & Response on anomalous behavior, advanced threats, and malware detection.
Implementing all these different capabilities individually is time consuming and expensive. Managed cloud security reduces the challenges by allowing you to manage these different cloud security aspects in an integrated and unified manner. You can manage all security aspects from a single interface for heightened visibility and control.
What is the difference between cloud security and traditional network security?
Traditional network security stacks protect network infrastructure connecting the organisation’s users and resources. In the past, the network clearly defined a perimeter with a fixed range of endpoints that could be comprehensively protected. However, cloud resources can be accessed from anywhere on any network and device, creating unlimited endpoints on the perimeter. Traditional network security architecture cannot scale elastically without significant costs and complexity.
Cloud security goes beyond perimeter protection to the individual protection of data and resources. It moves access controls and security directly into the cloud. You implement more granular measures like data protection, disaster recovery, encryption and access control.
Lumen Library
Insights and Resources
Questions? Let’s talk.
Contact our team and get answers you’re looking for.






