The Well-Architected Framework is a methodology developed by the cloud providers to help businesses build and operate secure, high-performing, resilient, and efficient cloud-based infrastructure on the cloud. It is a set of best practices, guidelines, and tools that can be used to evaluate, design, and improve the architecture of cloud-based solutions.
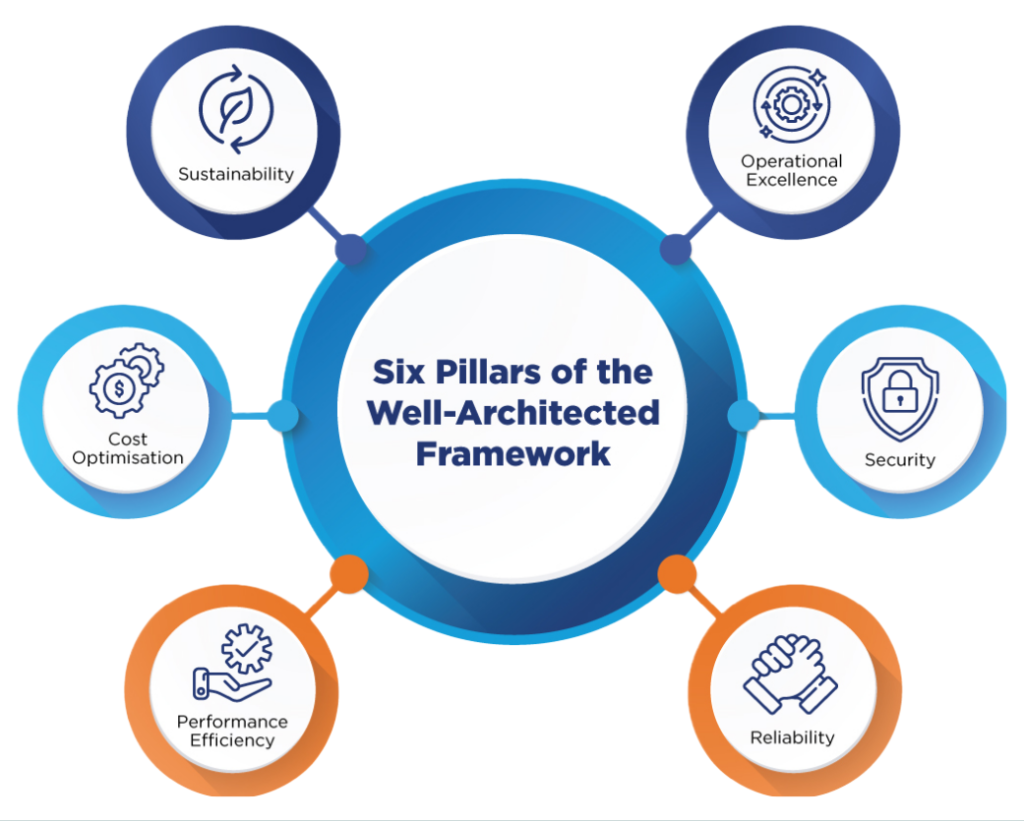
Well-Architected Framework is organised around six pillars: cost optimisation, security, reliability, operational excellence, performance efficiency and sustainability. Each pillar represents a different aspect of a well-architected system and includes a set of principles, considerations, and questions to guide businesses in designing and evaluating their systems.
Why is the Well-Architected Framework Important?
With the Well-Architected Framework, businesses can maximise the value of cloud services and minimise risks. They can improve the quality and efficiency of their cloud-based solutions, optimise their use of cloud resources, and achieve better business outcomes.
Helps to minimise risks: Enables businesses to identify and mitigate risks associated with cloud-based solutions. This helps organisations to minimise the risk of security breaches, system downtime, and other issues that could impact their business operations.
Ensures scalability and flexibility: The framework helps businesses to design solutions that are scalable and flexible, enabling them to adapt to changing business needs and handle increased workloads without compromising performance or availability.
Optimises resource utilisation: Businesses can optimise their use of cloud resources, resulting in lower costs and improved efficiency. By designing solutions that are well-architected, they can avoid unnecessary spending on resources and improve their return on investment.
Enhances performance and reliability: Build applications and workloads that are highly available, fault-tolerant, and performant. This helps to ensure that their accessibility and responsiveness, even in the face of unexpected events or changes in demand.
Facilitates compliance: Guidance on meeting regulatory and compliance requirements by helping businesses to avoid costly fines and legal issues.
Six Pillars of the Well-Architected Framework
1. Operational excellence
Operational excellence is about running and managing systems effectively and efficiently, to deliver business value to customers. It involves continuous improvement of operational processes, monitoring and measuring performance, and identifying and mitigating risks and issues proactively. Some key aspects of operational excellence include:
- Preparation: Establishing clear goals and objectives, defining roles and responsibilities, and creating effective communication and collaboration channels.
- Operations: Defining and implementing standardised, repeatable processes for deploying, monitoring, and managing systems, including automation and documentation.
- Change management: Implementing a formal process for managing changes to systems, including testing, validation, and approval procedures.
- Incident management: Establishing procedures for detecting, responding to, and resolving incidents, including escalation paths, communication plans, and post-mortem analysis.
- Continuous improvement: Implementing processes for monitoring and measuring system performance, identifying areas for improvement, and implementing changes based on feedback and metrics.
Essentially you should identify the most potent SASE use cases based on current requirements and understand the potential pitfalls of the deployment as well as the organisational and infrastructural limitations.
2. Security
The security pillar is concerned with protecting information and systems, including data confidentiality, integrity, and availability, by following best practices in the design and implementation of security controls. This is achieved by following several key principles including:
- Implementing a strong identity foundation: Implementing proper identity and access management, including authentication, authorisation, and permissions management.
- Applying security at all layers: Applying security controls at all layers of the architecture, including the application layer, network layer, and data layer.
- Automating security best practices: Automating security controls and best practices to reduce human error and increase consistency.
- Protecting data in transit and at rest: Implementing encryption and other security controls to protect data in transit and at rest.
- Ensuring secure application design: Incorporating secure coding practices and vulnerability testing in application development.
- Monitoring and responding to security events: Establishing processes for monitoring and responding to security events, including incident response planning and testing.
3. Reliability
The focus on reliability ensures that your system operates as intended and meets the needs of your customers and stakeholders. This means designing and implementing systems that are highly available, fault-tolerant, and resilient to failures. Reliability can be achieved by following several key principles, including:
- Designing for failure: Designing systems to withstand failures and minimise the impact of failures on users and stakeholders.
- Implementing automatic recovery: Implementing automatic recovery mechanisms to minimise downtime and restore service quickly.
- Scaling horizontally: Designing systems that can scale horizontally to accommodate changes in demand and traffic.
- Testing for reliability: Implementing testing strategies that ensure the system is reliable, including load testing, stress testing, and chaos engineering.
- Managing change: Implementing processes for managing changes to the system, including testing, validation, and approval procedures.
- Monitoring and responding to events: Establishing processes for monitoring and responding to events, including alerts and notifications, and incident response planning and testing.
4. Performance efficiency
Performance efficiency refers to the ability of a system to use computing resources efficiently to meet its performance requirements. This includes optimising processing, storage, and network resources to deliver the desired level of performance, scalability, and availability. The following design principles should be considered to achieve good performance efficiency:
- Selection of the right resources: Select the appropriate resources and services that match the application workloads requirements, such as memory, CPU, and storage.
- Scalability: Designing the system to scale up or down as per the demand to ensure that the system can handle sudden spikes in traffic without affecting performance.
- Performance monitoring: Implementing monitoring and alerting to identify performance bottlenecks, track usage trends, and ensure that performance requirements are being met.
- Optimisation: Continuously optimising the system by identifying and addressing performance issues, such as reducing latency, improving response time, and optimising resource utilisation.
5. Cost optimisation
Cost optimisation refers to the process of optimising the costs associated with running workloads on the cloud. This includes identifying and eliminating waste, identifying cost-effective solutions, and ensuring that resources are being used efficiently. Businesses should consider the following design principles for cost optimisation:
- Cost-aware architecture: Designing architectures that are optimized for cost by selecting the appropriate services and resources that match the workload requirements.
- Right-sizing: Right sizing of resources such as instances, storage, and databases to match the workload requirements, avoid over-provisioning or under-provisioning.
- Optimising Usage: Optimising usage of resources by taking advantage of features such as auto-scaling, reserved instances, spot instances, and using low-cost storage tiers such as Glacier for infrequently accessed data.
- Managing waste: Managing waste by eliminating underutilised or unused resources, consolidating resources, and avoiding over-provisioning.
6. Sustainability
Sustainability is an essential consideration in the framework, as it aims to ensure that cloud-based solutions are environmentally responsible and help reduce the carbon footprint of businesses. Some key aspects of the Well-Architected Framework that promote sustainability include:
- Resource optimisation: By using automation tools to scale resources up and down based on demand, organisations can ensure that they only use the resources they need and avoid over-provisioning, which can lead to wasted energy.
- Efficient design: The importance of designing cloud-based solutions that are efficient and minimize energy consumption. For example, using serverless architecture can reduce the need for infrastructure and lower energy consumption, as resources are only used when needed.
- Renewable energy: The framework encourages businesses to use cloud providers that use renewable energy sources to power their data centres. This can help reduce the carbon footprint of the business and contribute to a more sustainable future.
- Green initiatives: The framework encourages businesses to take a holistic approach to sustainability by implementing green initiatives in all areas of their business, including their cloud-based solutions. This can include using sustainable materials for hardware, promoting telecommuting and remote work to reduce carbon emissions, and encouraging recycling and waste reduction.
Top Benefits of Implementing the Well-Architected Framework
Here are the top benefits for business that build their cloud-based systems in line with the Well-Architected Framework:
- Improved security posture: Allows businesses to identify potential security vulnerabilities in your cloud infrastructure and provides guidance on how to mitigate them. By following best practices and implementing the necessary security controls, you can improve your overall security posture.
- Consistent security practices: By having a consistent approach to security across your cloud infrastructure, all teams and applications will follow the same security practices, which reduces the risk of security gaps or oversights.
- Risk reduction: With an improved security posture, potential security risks can be easily mitigated before they become actual security incidents. This reduces the risk of data breaches, data loss, and other security incidents.
- Compliance: Many regulatory frameworks, such as GDPR and HIPAA, require businesses to implement security controls and best practices. By implementing the Well-Architected Framework, you can ensure that you meet these compliance requirements.
- Cost savings: Avoid costly downtime, security breaches, and other cybersecurity-related issues. This can ultimately help you save money and manage cost efficiently in the long run.
- Reliability: Designing and building cloud-based systems that are resilient to failure. This includes implementing redundant components and deploying systems across multiple availability zones.
- Sustainability: Optimising the use of resources and minimizing waste to fulfil your environmental, social & governance (ESG) goals. By designing efficient systems, you can reduce your environmental impact and promote sustainability.
How to Implement the Well-Architected Framework
It is important to note that implementing a Well-Architected Framework is an ongoing process and requires continuous attention and improvement. You can start by following the general steps:
- Identify your goals: Determine the specific security, reliability, performance, and cost optimisation goals you want to achieve in your cloud environment.
- Evaluate your current environment: Assess your current cloud infrastructure to identify areas where you can improve across the pillars in the Well-Architected Framework.
- Identify best practices: Review the Well-Architected Framework or any other framework that suits your cloud environment and identify the best practices that can help you achieve your goals.
- Prioritise improvements: Focus on the immediate improvements you want to make based on the potential impact on your business operations.
- Develop an implementation plan: Determine the best practicess for implementation, including timelines, budgets, and resources needed.
- Implement and test: Test the implementations to ensure that they meet your immediate requirements as well as business goals.
- Monitor and iterate: Continuously monitor your cloud environment and iterate on your implementation plan as necessary to ensure that you are achieving your goals.
An Example
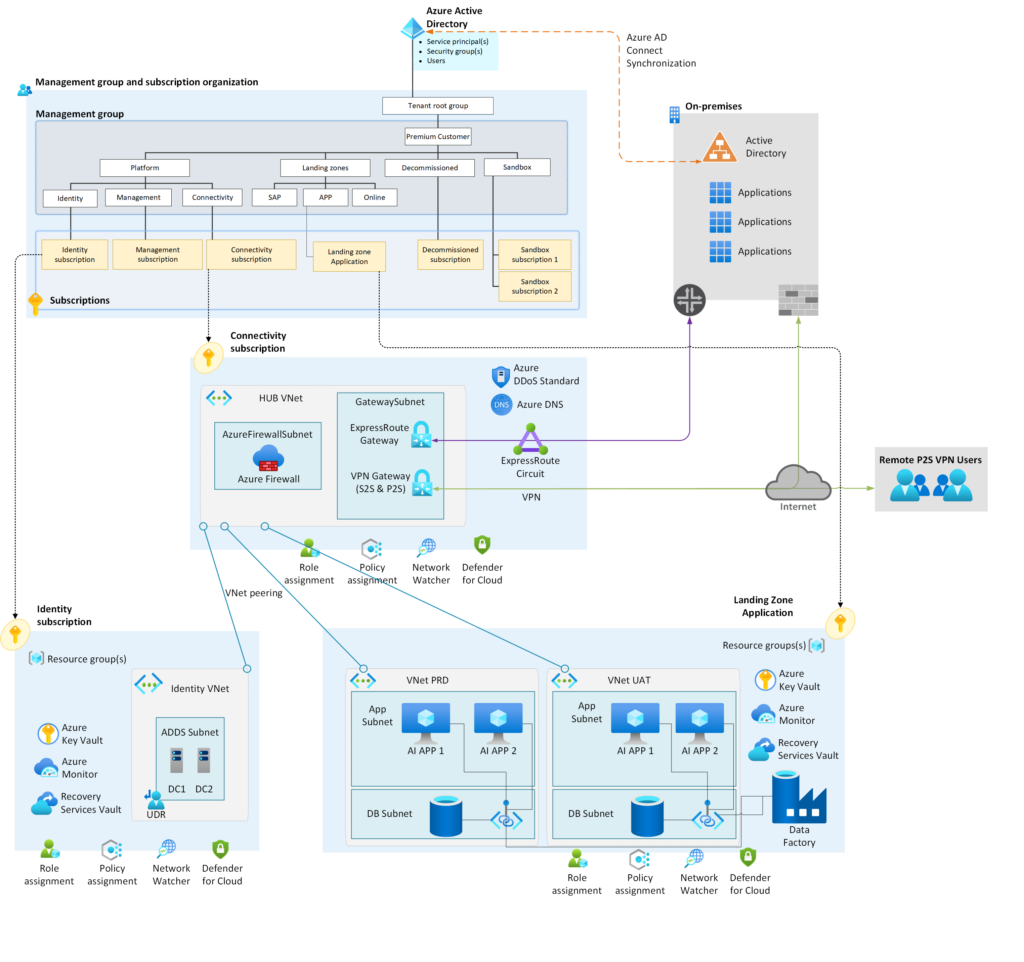
A leading logistics company was facing challenges with managing their AI application on Azure (POC) subscription, which was becoming increasingly complex, non-compliant, and costly to maintain. They decided to migrate their AI application from the existing subscription to the new Azure subscription, embracing the Well-Architected Framework to ensure their cloud-based solution was reliable, secure, efficient, and cost optimise.
Key Challenges
The key challenge in migrating the AI application to Azure was ensuring a seamless transition without impacting the company’s business operations. Additionally, the logistics company needed to optimise the application’s usage of Azure resources to minimize costs and meet their security and cost optimisation goals.
Solution
To overcome these challenges, the logistics company engaged a team of Lumen cloud specialists to plan, design, and implement the migration. Lumen identified the components of the AI application that needed to be migrated and selected the appropriate Azure services to host the application, including Azure Virtual Machine, Azure Data Factory (ADF) and Azure SQL Database.