In today’s digital world, network security is one of the most critical factors that determine the success of any organisation.
With the increasing number of cyberattacks, organisations are very keen to implement an effective network security layer as it has become more critical than ever before. A key component of a robust security infrastructure is the third-party firewall appliance.
In this content, you will learn more about the firewalls, its selection criteria, design principles and its applications in both enterprise networks and cloud-hosted data centres.
What is a Third-Party Firewall?
A third-party firewall is a security device that is installed between the internal network and the Internet in general. However, firewalls are also placed in the internal networks to have more granular restrictions between different application environments.
It acts as a barrier between the two networks, allowing only authorised traffic to pass through while blocking all unauthorised traffic with predefined set of rules. Third-party firewalls are essential for securing corporate networks, as they provide an extra layer of protection against external threats.
A firewall can be hardware, software running on a virtual machine (VM), software-as-a service (SaaS) firewall or virtual firewall instances running on the public cloud.
Over the years, firewalls have evolved beyond simple packet filtering and stateful inspection model to next-generation firewalls which are capable of blocking modern threats, such as advanced malware and application-layer attacks. According to Gartner, a next-generation firewall must have the following features:
- Intelligence-based access control with stateful inspection
- Integrated intrusion prevention system (IPS)
- Application awareness and control to see and block risky apps
- Upgrade paths to include future information feeds
- Techniques to address evolving security threats
- URL filtering based on geolocation and reputation
In the past, the firewall device used to sit on the network edge to protect the organisation’s internal data and data-processing assets. But times has change, the digital evolution across private cloud and public cloud along with the increasing number of remote workers have expanded the network perimeter.
Firewalls must enforce common policy with control points across the company locations. With a comprehensive firewall strategy, having consistent security controls can better enable organisations to meet their security requirements.
Why implement a Third-Party Firewall?
There are several reasons why an organisation should implement a third-party firewall:
- Protection against cyber threats: Provides protection against cyber threats such as viruses, malware, and other forms of malicious activity.
- Enhanced network security: An extra layer of security for the corporate network, making it more difficult for hackers to gain unauthorised access.
- Compliance: Many industries have regulatory requirements that mandate the implementation of a third-party firewall. Failure to comply with these requirements can result in hefty fines and legal penalties.
How to implement a Third-Party Firewall?
Each organisation may have different firewall implementation methodologies/stages based on their existing business and technical requirements. However, the following are the five key important steps for any firewall implementation project.
1. Determine Firewall Requirements:
The first step is to determine your organisation’s firewall requirements. This involves identifying the types of traffic that need to be allowed through the firewall, as well as the types of traffic that need to be blocked. The following firewall design principles can help to have most secure firewall system in place.
- Finalise the security controls for your organisation needs: This involves collecting security requirements, evaluating the current security posture, and deciding how firewalls can address any concerns.
- Choose your firewall policy requirements: This activity centres around the identification of applications, resources, and services that you want to protect.
- Decide where the firewalls will be deployed: Strategically decide the firewall device placement in the network. This should be specifically focused on safeguarding the communications and systems which was identified in the earlier steps. For example, we can use a stateful inspection firewall at the perimeter of the network and can be placed between the Internet L2 switch and ISP routers.
2. Choose a Third-Party Firewall Solution:
Once you have identified your organisation’s firewall requirements, the next step is to choose a third-party vendor firewall solution that suits your organisation. There are many different firewall solutions available on the market, so it is important to choose the one that is best suited to your organisation’s needs. Here are some factors to consider when choosing a firewall solution:
- Access Control and applications traffic visibility: Consider which applications and which users within your network are authorised to access as well as the visibility you need. The firewall should be application-aware to support the above-mentioned feature and choose the firewall accordingly.
- Threat Prevention: The device should be a next-generation firewall (NGFW) which not only controls applications access, but it can also scan applications to ensure they do not present a threat.
- Firewall Capacity and throughput: Applying filters and processing information can significantly limit throughput. When selecting the next generation firewall, choose the one that gives the required throughput, IPS scanning and number VPN tunnels to run the security operations smoothly.
- Remote Access for telecommuters: The volume of the remote workers today has increased tremendously. When sizing the firewall, organisations need to make sure that the firewall is capable of acting as remote access VPN server by considering the required capacity, licensing, and VPN client requirements.
- High Availability (HA): Firewalls have become critical infrastructure components on the network, it is important to ensure that the firewall and the functionality that it provides, is always available and accessible. This can be achieved by having redundant firewalls in active/passive or active/active mode based on the business requirements.
3. Implement the Firewall Solution:
Once you have chosen a third-party firewall solution, the next step is to create the detailed design, install, and configure the firewall.
- Design: Creating security architecture diagrams, defining the rules, polices and identifying the policy enforcement points.
- Installation: Physically installing the firewall on your network racks and configure basic settings to bring it on your corporate network.
- Configuration: At this stage, the firewall implementation engineer will do a detailed configuration of the network access controls and policies required for threat prevention, logging, monitoring, and other settings to match your organisation’s requirements.
4. Test the Firewall:
After the firewall has been installed and configured, it is essential to test it to ensure that it is working correctly. This involves running a series of installation, functional and user acceptance test cases to ensure that the firewall is implemented as per the agreed design and blocking all unauthorised traffic while allowing authorised traffic to pass through.
5.Monitor and Maintain the Firewall:
It is essential to monitor and maintain the firewall regularly in terms of the rules and policies. This also involves keeping the firewall software updated with the latest security patches and firmware updates, as well as monitoring the firewall logs for any signs of unauthorized access or other security breaches.
Deployment scenarios
As we have now understood the various stages of the firewall implementation project, here are two deployment scenarios to illustrate third-party firewall implementation:
Third-party firewall deployment for enterprise data centre perimeter security
The Internet edge is the point where the organisation’s network connects to the Internet. This is the perimeter of the network where a line is drawn between the public Internet and the private resources contained within the company’s network.
Firewall security is an integral part of every Internet Edge deployment today—to protect information while meeting the need for secure reliable networks, and to enforce policy to maintain security standards.
In the below example, the perimeter security architecture designed with two redundant third-party firewalls to address requirements for high availability, and they are configured in an active/standby pair to ensure that Internet access is minimally impacted by firewall software maintenance or hardware failure.
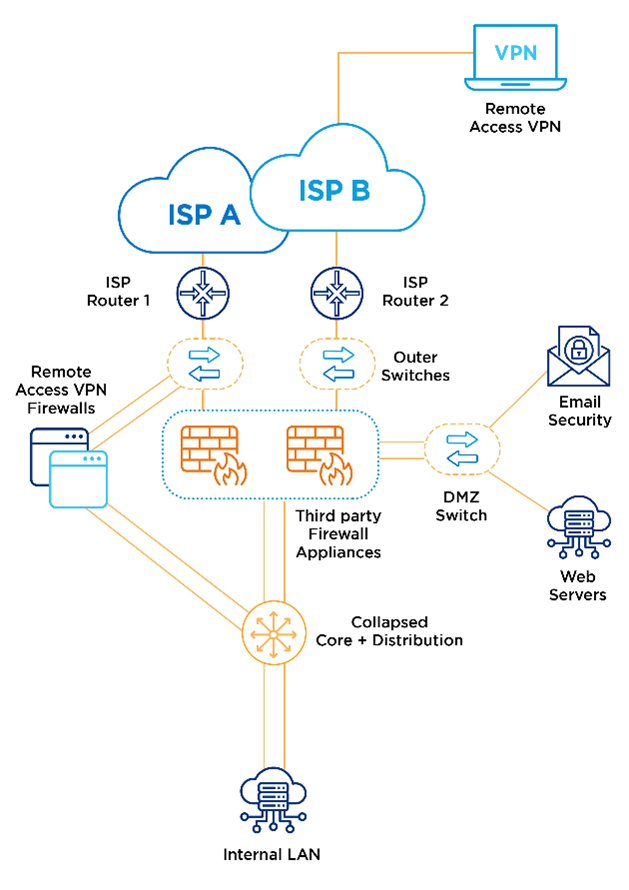
This Internet edge firewall design uses dual Internet connections for resilient access to the Internet. Remote Access VPN is provided by a separate pair of VPN firewalls, to provide additional scalability and operational flexibility.
Third Party Firewall deployment in public Clouds
In recent years, enterprise applications are being migrated to public cloud VMs and containers instead of on-premise hosted severs. This is extending the corporate network to the public cloud which increased cyber risk as well, hence all the traffic to and from the public cloud hosted workloads have to be screened and protected. This is where cloud native firewalls are helping to secure ingress, egress, and east-west traffic to detect and stop malicious activity across accounts in the public cloud environment.
Today all the major public cloud providers (CSPs) offer cloud native firewalls like AWS network firewall, Azure Firewall, etc., However, many enterprise users prefer to leverage their existing on-premises firewall technology or want to get started in public cloud by using their existing firewall expertise.
To address the specific customer requirements, the leading third-party firewall vendors have versions of their software firewall in the public cloud marketplace that can be deployed by either bring-your-own-license (BYOL) or pay-as-you-go pricing models. This makes it easy to get up and running with your preferred firewall vendor leveraging their optimised cloud compute instance templates available in the public clouds. These third-party virtual appliances can be integrated well with existing public cloud network components.
Just to understand with an example on a third-party firewall virtual appliance deployment into an AWS environment. There are couple of approaches available to deploy third party firewall virtual appliances on AWS.
The commonly used methods are centralised and distributed deployment model:
- In the centralised deployment, redundant firewalls will be running in separate “security or inspection VPC” where all the traffic will get forwarded to the third-party firewall virtual instances deployed there
- In the distributed model, there will be multiple firewalls deployed in each of the VPCs, and the traffic is screened against predefined rules and policies at each VPC level
The following diagram explains about the centralised firewall deployment model in dedicated security VPC through the VPN attachment to the Transit Gateway (TGW):
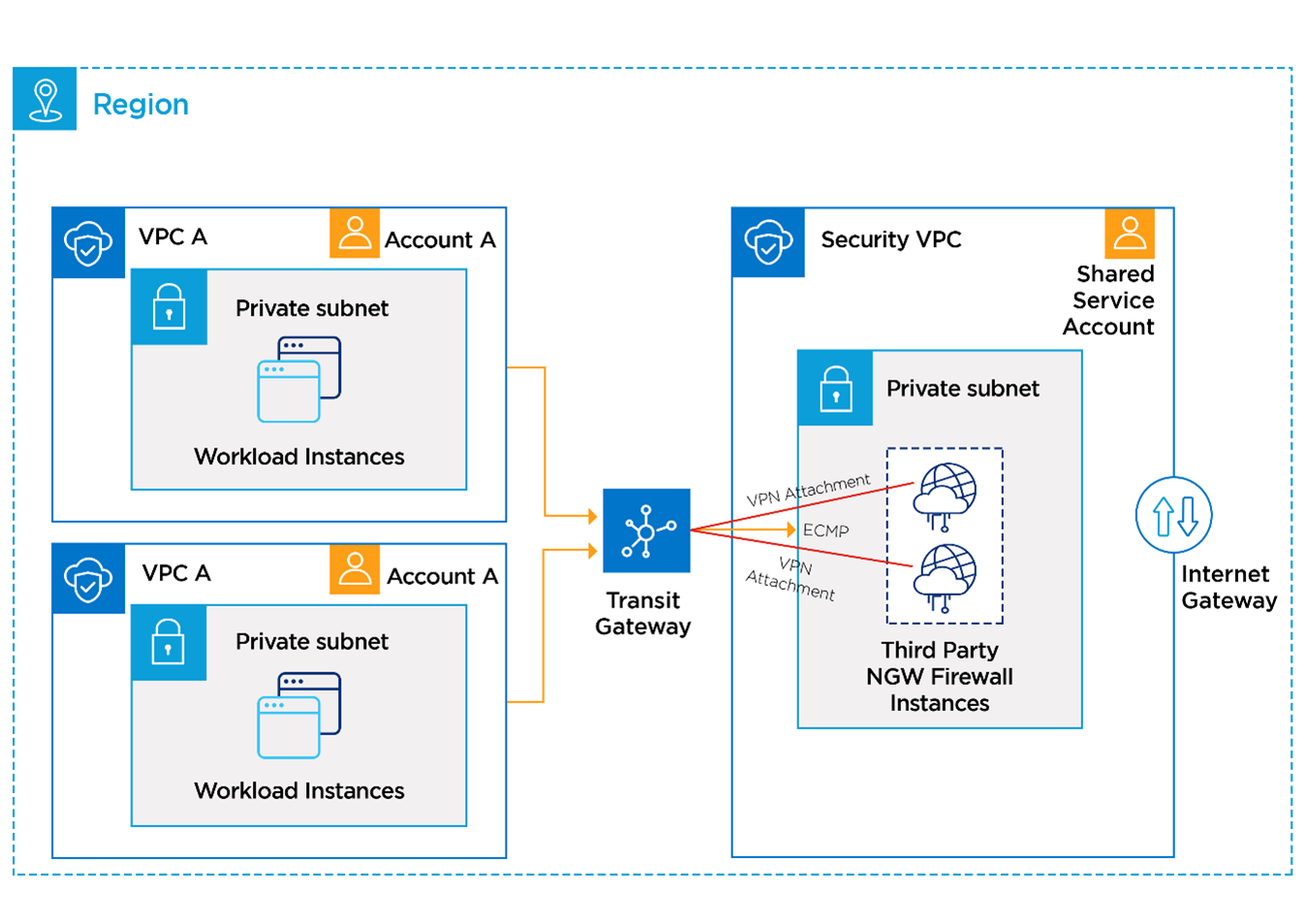
In the above architecture, a default route will be configured in each VPC route table with TGW as the destination. In the transit gateway, VPC to VPC route table will have a default route that directs traffic to the ECMP load-balance VPN connections with each VPN attachment having a maximum throughput of 1.25 Gbps. BGP routing protocol can be configured over the VPN to have automatic failover in the case of any issues with a particular firewall instance and during maintenance activities.
The traffic then terminates on a firewall and gets source NAT (SNAT) applied to maintain flow symmetry. Internet bound traffic goes out to the Internet Gateway (IGW) and VPC traffic routes back into the TGW to the destination VPC inside the AWS environment.
Partnering for success
Implementing a third-party firewall is essential for ensuring the security of your corporate network.
With the Lumen Third Party Firewall implementation service, we can partner with you to ensure successful implementation that provides an extra layer of protection against cyber threats.